Company benefits
We’ve Helped Hundreds of Clients Work Faster, Smarter and Safer.
Keeping your business safe is hard when you don't know what's against you. Today more than ever, enterprises are beset by cybersecurity threats ranging from phishing attacks to crippling ransomware.
That's why we created a cutting-edge end-to-end security assessment and management platform to help organizations tighten their security exposure before threat actors can exploit them.
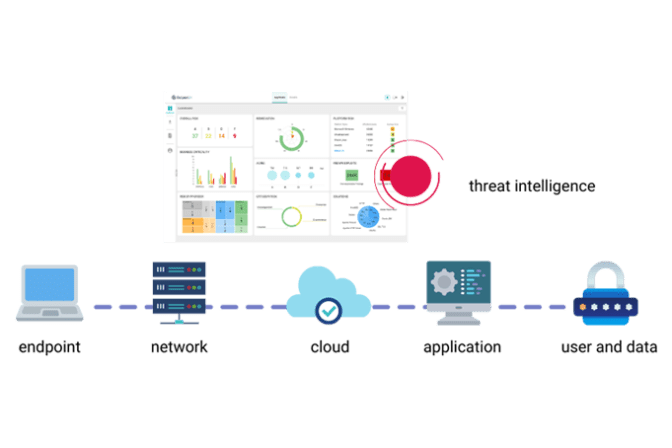
Complete Security Offering
Total Peace of Mind via Our Managed, Proactive and Complete Security Offering.
At IT Max Global, we distilled our 15-year experience to replace the complicated process of identifying and managing cybersecurity risks across the technology stack with a single end-to-end solution, providing our security clients with a managed, scalable service that wins them complete peace of mind to focus on wins - instead of potential losses.
Unified Endpoint Management (UEM)
See All Devices. Secure All Devices. Manage All Devices. Centrally & Efficiently.
Let IT Max manage, secure, and deploy your corporate resources and applications on any device, remotely. Our UEM solution provides real-time monitoring, alerts, and updates, ensuring your devices are always up-to-date and secure. IT Max's UEM improves productivity by allowing employees to use preferred devices and apps, while maintaining security. It unifies traditional and mobile device management, reducing costs and ensuring compliance, with a single user interface to manage, configure, and secure all devices. This results in better user experiences and zero compromise on protection.
Automate deployments, personalize user workspaces and fix issues quickly, and feel confident in employing a BYOD policy.
Access Management
Unlock the Power of intelligent Access.
IAM is the key to unlocking the power of secure access for your organization. It ensures that only authorized users have access to sensitive information, preventing unauthorized access, breaches, and data loss.
But it's not just about security. IAM also streamlines the process of granting and revoking access, allowing you to manage user access more efficiently. Plus, with IAM, you can provide personalized access to systems and applications, resulting in a better user experience.
Don't wait for a data breach to happen. Take control of access to your systems and data, and rest easy knowing that your sensitive information is secure and that you are in compliance with industry regulations.
Security Operations Center (SOC)
Efficient and affordable security operations management, delivered in an as-a-service model.
We offer SOC as part of our managed security services, bringing a high level of security that's cost-effective for every company. Our SOC-as-a-service is specifically suitable for organizations that want to have an in-depth understanding and complete control over what is happening within their network, both on premise and in the cloud, to be able to respond immediately to possible threats. With our SOC, clients can detect potential threats within corporate networks, ranging from hackers and malware to employees who consciously or intentionally seek access to confidential information. With our dedicated cybersecurity team on the lookout 24x7x365, you get a powerful and scalable Security Information and Event Management (SIEM) solution, reducing your risk and exposure, enabling your company to take action quickly before the spread of an attack and without the need for personnel investment, management and/or maintenance.
Government-grade security: Our SOC is designed to operate within high security contexts, especially suitable for governmental or very security-conscious environments. We offer various service tiers, from a low barrier-to-entry model to a full-service SOC.
Network Security
Ensure Fast, Uninterrupted Access to Your Network Assets. Meet Regulatory Requirements.
We offer a comprehensive range of network security services. Compared to handling it in-house, relying on a dedicated MSP wins you expert knowledge, cost savings, 24/7 monitoring, proactive security, and regulatory compliance. This allows you to focus on your core business activities while having peace of mind that your network is secure and highly performant.
Our team of experienced engineers will monitor your network around the clock to ensure optimal performance and availability. We use advanced tools and techniques to quickly identify and resolve any issues that may arise, minimizing downtime and maximizing your network's performance.
The solution includes next-gen firewalls (with smart VPN and WAN optimization for fast internet access), web and email filtering, malware and advanced threat protection, anti-spam protection, and network access control. We make sure you're secure from breaches and attacks.
$4.24 Million USD: The Average Cost of a Data Breach in 2021.
The common rule of thumb suggests that for every 100 employees, you should have at least one full-time IT staff member.
But between providing technical support to employees, administrative tasks, troubleshooting, upgrades to hardware or software, network infrastructure upgrades and other day-to-day tasks, the time that can be dedicated to securing your assets and looking out for cyberthreats is minimal.
That's why it is crucial to have a dedicated cybersecurity partner looking out for your enterprise.